Ultimate Guide to Digital Safeguarding Reporting Tools
Explore the essential digital safeguarding tools for nonprofits to protect sensitive data, enhance compliance, and improve reporting processes.

Digital safeguarding tools are critical for nonprofits, especially those working with child sponsorship programs, to protect vulnerable individuals and ensure secure operations. These tools address online risks, streamline reporting, and enhance data security while meeting privacy regulations. Here's why they're indispensable:
- Protects Children Online: With a child accessing the internet every half second, safeguarding tools help mitigate risks like exploitation and data breaches.
- Streamlines Reporting: Simplifies processes for staff and volunteers to report concerns, improving accountability and risk management.
- Data Security: Implements encryption, access controls, and compliance with laws like GDPR and CCPA to safeguard sensitive information.
- Addresses Cyber Threats: Tackles rising threats like phishing, ransomware, and AI-driven attacks, which are increasingly targeting nonprofits.
- Supports Staff Training: Ensures teams are equipped to recognize and respond to security risks effectively.
Key features include secure case management, customizable workflows, and compliance with U.S. privacy standards. Platforms like HelpYouSponsor offer tailored solutions, integrating security with donor management tools to build trust and operational efficiency. Nonprofits can strengthen their digital safeguards by assessing vulnerabilities, training staff, and continuously monitoring systems.
Things to Consider in Creating an Effective Online Reporting System
Key Features of Digital Safeguarding Tools
The effectiveness of digital safeguarding tools lies in their ability to go beyond basic reporting, creating a secure and efficient environment for managing sensitive information. These tools are designed to streamline reporting processes, ensure data protection, and support compliance with relevant standards.
Secure Case Management and Reporting
A reliable safeguarding tool prioritizes secure case management by implementing multiple layers of protection that go far beyond simple password security.
- Administrative safeguards: At the core of security is a set of clear policies that define access rights and user responsibilities. For instance, your organization should document who can access specific information, under what circumstances, and for how long. According to the HIPAA Security Rule, these policies must be retained for at least six years.
- Physical safeguards: Protecting the physical spaces and devices where sensitive data is stored is equally important. This can include using cable locks, privacy screens, and auto log-off features, as well as enforcing strict visitor protocols for non-employees.
- Technical safeguards: Advanced technology solutions like encryption, secure key storage, and automatic audit trails are essential. Regular risk assessments can identify potential vulnerabilities before they become issues.
"Protecting patient data is at the heart of HIPAA security measures, and understanding how technical safeguards HIPAA requirements work is crucial for any healthcare organization." - Kevin Henry, HIPAA
These measures work together to create a robust framework for managing sensitive cases securely and efficiently.
Customizable Workflows and Forms
Every organization operates differently, so safeguarding tools must be adaptable. Customizable workflows simplify routine tasks, reduce manual errors, and speed up case resolution. Digital forms guide users step-by-step, ensuring submissions are complete and compliant.
Additionally, these workflows enhance transparency and accountability. By attaching timestamps, user IDs, and location data to each record, organizations can easily track case progress. This detailed tracking not only helps leaders identify trends early but also aids in making informed decisions about resource allocation and policy adjustments. This flexibility ensures that safeguarding protocols are followed consistently and effectively.
Compliance with U.S. Privacy and Data Protection Standards
For nonprofits and other organizations managing sensitive data, compliance with U.S. privacy and data protection laws is non-negotiable. These regulations require strong encryption, strict access controls, regular backups, and secure IT infrastructure .
The Federal Trade Commission enforces data security by holding organizations accountable for inadequate practices. Techniques like Data Loss Prevention (DLP) help prevent unauthorized access or data leaks. Proper authentication ensures that only authorized individuals can access sensitive information.
In 2022, over 2,000 publicly disclosed data breaches were reported, with 60% caused by hacking and 95% linked to human error. This highlights the need for a combination of technical safeguards and continuous employee training.
Organizations can enhance their security by adopting a Zero Trust Architecture, which constantly verifies user and device identities. Additional measures like tokenization, pseudonymization, and hash functions ensure data integrity and protection. Regular reviews of data retention policies help eliminate outdated information, while immutable storage solutions guard against ransomware and unauthorized changes.
To further strengthen security, organizations should conduct regular audits, implement comprehensive security policies, and train staff to recognize and report suspicious activity. Contingency plans for data backup and disaster recovery ensure access to critical information during emergencies. These practices not only safeguard data but also uphold the ethical standards vital for digital safeguarding efforts.
Security and Privacy Best Practices
Continuing from our discussion on secure case management, let’s explore effective strategies to bolster cybersecurity and safeguard sensitive nonprofit data. With cyber threats evolving rapidly, understanding the risks and adopting proven defenses can preserve donor trust and prevent costly setbacks.
Cybersecurity Risks for Nonprofits
Nonprofits are increasingly targeted by cybercriminals due to limited budgets and weaker security measures. Alarmingly, there has been a 30% year-over-year increase in weekly cyberattacks in 2024.
While traditional threats like phishing and ransomware persist, attackers are now deploying AI-driven tactics such as deepfakes, smishing, and quishing. These sophisticated methods can bypass even well-trained staff, highlighting the ongoing vulnerability of human error.
In 2021, nonprofits ranked as the second most targeted sector for cyberattacks, making up 31% of all nation-state attack notifications. A more recent study found that 41% of Geneva-based nonprofits experienced cyberattacks, and 68% reported data breaches in the past three years.
One high-profile example is the January 2022 breach of the International Committee of the Red Cross (ICRC). Hackers infiltrated the "Restoring Family Links" program, compromising the personal data of 515,000 vulnerable individuals. The attackers used tools typically associated with advanced persistent threat groups.
The human factor remains a major challenge. In 2024, 68% of breaches involved human-related errors like phishing or accidental mishandling of data. This underscores the need for robust security practices, which we’ll outline below.
Protecting Sensitive Information
Protecting nonprofit data starts with a combination of employee education, strong authentication protocols, and technical safeguards. Training staff to recognize phishing attempts, create secure passwords, and identify suspicious activity is a crucial first step.
Organizations should enforce unique, complex passwords and adopt multi-factor authentication (MFA) to deter unauthorized access. Additionally, encrypting sensitive data during transmission and storage ensures that, even if intercepted, the information remains inaccessible to attackers.
Regular backups are another key defense. Storing critical data offsite and testing backups frequently helps nonprofits recover quickly from ransomware attacks or system failures. To minimize internal risks, role-based access controls limit who can view or modify sensitive information.
"Many of our small- to mid-size clients struggle with where to start and how to allocate resources to identify cyber vulnerabilities. We've developed a cybersecurity assessment for organizations like this, with average price points of $10 – 15k as of 2025, to help our clients get started on the road to enhanced security." – Kelsey Vatsaas, Managing Principal, Nonprofit, CLA
For more advanced protection, some nonprofits are leveraging AI tools to detect deepfakes and analyze unusual communication patterns. Regular security assessments are also essential for identifying vulnerabilities before they can be exploited. Together, these measures help mitigate both financial risks and reputational damage.
Financial and Reputational Impacts of Security Lapses
The financial fallout from a security breach can be devastating, with costs reaching up to $2 million. These expenses include incident response, legal fees, regulatory fines, and credit monitoring services. For smaller nonprofits, the lack of resources compounds the challenge - 56% of NGOs lack a cybersecurity budget, and 70% feel unprepared to handle an attack.
Rebuilding public trust after a breach is even harder. Take the Australian Red Cross, for example. In 2016, a data breach exposed the health information of over 550,000 blood donors due to human error and poor data management by a contractor. This incident severely damaged the organization’s reputation, leading to reduced donations and volunteer participation.
Legal compliance adds another layer of complexity. As of May 2025, 13 states have enacted data privacy laws, with more expected later in the year. States like Colorado and New Jersey do not exempt nonprofits, while new laws in Tennessee, Minnesota, and Maryland will take effect on July 1, July 31, and October 1, 2025, respectively. Staying updated on legal requirements is essential to avoid penalties.
Ultimately, prevention is far less costly than dealing with the aftermath of a breach. By investing in cybersecurity measures, ongoing staff education, and compliance readiness, nonprofits can protect their data and continue their mission without disruption.
Digital Safeguarding Platforms Overview
In today’s landscape of cybersecurity threats, digital safeguarding platforms have become essential for protecting data and simplifying compliance. These tools combine advanced security features with user-friendly designs, allowing organizations to focus on their primary goals without compromising on safety. This section explores how tailored solutions, like HelpYouSponsor, meet these needs effectively.
HelpYouSponsor as a Complete Solution
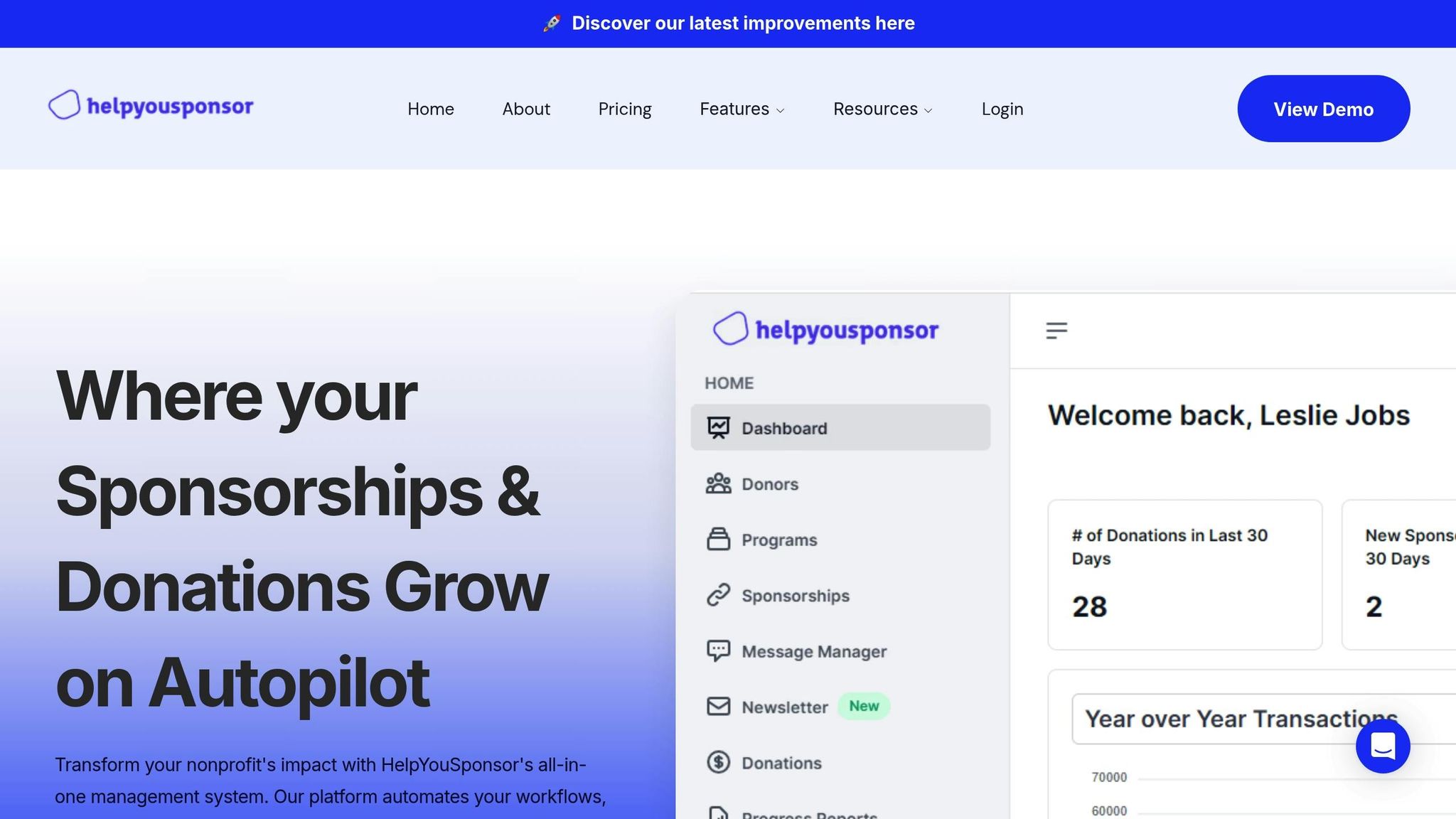
HelpYouSponsor (HYS) is specifically designed for nonprofits, offering a robust platform that enhances sponsorship programs, fundraising efforts, and donor management. The platform takes a privacy-first approach, ensuring compliance with regulations like GDPR and CCPA while using PCI-compliant encryption and role-based access controls to protect sensitive donor information. Customizable admin permissions further strengthen its security framework.
HYS automates financial compliance tasks and simplifies reporting, reducing the need for manual processes. It also provides detailed controls for payment processing, ensuring secure and efficient transactions.
Beyond security, HYS helps nonprofits build stronger donor relationships. Features like automated thank-you messages and newsletters foster consistent communication, which has been shown to boost donor retention rates to 53%. The platform integrates seamlessly with widely used tools like Stripe, Mailchimp, and Zapier, making it a flexible choice for nonprofits. This is particularly important given that 76% of nonprofits anticipate being targeted by cyberattacks in the coming year.
Comparison of Key Tools
When evaluating safeguarding platforms, nonprofits should consider several key features. Here’s how HelpYouSponsor compares to other platforms on critical criteria:
| Feature Category | HelpYouSponsor | Key Considerations for Other Platforms |
|---|---|---|
| Data Security | PCI-compliant, encrypted, role-based access controls | Look for end-to-end encryption and secure data storage |
| Compliance Support | GDPR, CCPA, and automated financial compliance | Ensure support for relevant U.S. privacy laws and compliance documentation |
| Access Controls | Granular admin permissions, customizable user roles | Verify data access is limited to necessary personnel |
| Integration Capabilities | Seamless integration with Stripe, Mailchimp, Zapier | Check compatibility with existing nonprofit tools and payment gateways |
| Transparency Features | Built-in reporting and donor communication tools | Platforms should support clear data collection practices |
| Staff Training Support | Privacy-first design with intuitive interfaces | Look for platforms offering staff training on data privacy |
This comparison highlights the importance of balancing strong security measures with ease of use. As Rick Cohen, Chief Operating Officer of the National Council of Nonprofits, advises:
"The bottom line is to treat information shared by the people your nonprofit engages the same way you'd want your own information to be treated".
Nonprofits should prioritize platforms that collect only the necessary data and uphold transparent privacy policies. Platforms must also clearly communicate how data is collected, used, and safeguarded. With 80% of adults globally expressing concerns about online privacy, choosing a platform with robust privacy protections is not just about meeting regulations - it’s about earning and maintaining trust. Nonprofits should thoroughly research options, read reviews, and select solutions that align with their unique needs while demonstrating a strong commitment to data security.
How to Implement and Optimize Digital Safeguarding Tools
After exploring the key features of digital safeguarding, the next step is putting these tools into action. Successful implementation involves assessing your organization's needs, equipping your team with the right knowledge, and consistently monitoring and refining your approach.
Assessing Organizational Needs
Before diving into any digital safeguarding solution, it’s crucial to understand your organization’s specific vulnerabilities. Start with a thorough audit of your website, data systems, and integration capabilities. Look for weak spots like outdated software, weak passwords, or unencrypted data that could leave your organization exposed to cyber threats.
Pay close attention to your website’s user experience, mobile compatibility, accessibility, and the security of any plugins you use. Similarly, review your data systems to confirm that information is accurate, standardized, and securely backed up. Conducting a risk assessment is equally important - map out who has access to sensitive data and how that information moves through your organization. This will help you identify potential weak points in your security.
"This questionnaire identifies areas of both unknown and known weakness and concerns for the optimal health and growth of this organization. This DAT has been an amazing opportunity to clarify need, reestablish goals, and monitor digital transformation."
- Bianca Deloach, Executive Director, Prevail Outreach Ministries, Inc.
Budgeting is another key step. Set clear financial goals and choose tools that can scale with your organization’s growth. Weigh the cost of safeguarding tools against the potential financial and reputational damage a security breach could cause. Once you’ve identified vulnerabilities, focus on training your team and updating policies to address these gaps.
Training Staff and Updating Policies
Even the most advanced tools are only as effective as the people using them. That’s why training your staff to recognize threats, create strong passwords, and spot phishing attempts is essential. Regular training ensures your team stays informed about evolving cyber risks and understands their role in keeping your organization secure.
Make it mandatory to use strong, unique passwords and implement multi-factor authentication. Develop a comprehensive cybersecurity policy that outlines acceptable use guidelines, incident reporting procedures, and protocols for responding to threats. This policy should also include clear instructions on how to handle sensitive data - covering everything from collection and storage to disposal and protection.
Create a culture of cybersecurity awareness. Encourage employees to report suspicious activities without fear of blame, fostering a sense of shared responsibility. Training should also include hands-on sessions on how to use your safeguarding tools effectively, so your team understands not just the how but also the why behind these measures.
Monitoring and Continuous Improvement
Digital safeguarding isn’t a one-and-done task - it’s an ongoing effort. Regular security audits and risk assessments are critical for spotting issues before they become major problems. Using structured change management strategies can lead to better outcomes and even cost savings over time.
Feedback is another vital component. Create channels for staff and stakeholders to share their experiences with digital processes and highlight any challenges. Use data analytics to track key performance indicators like incident response times, user compliance rates, and system uptime. These metrics will help you measure the effectiveness of your safeguarding measures.
"The message of the Kaizen strategy is that not a day should go by without some kind of improvement being made somewhere in the company."
- Masaaki Imai, Pioneer of Kaizen
Involve your team in the process of continuous improvement. Encourage them to identify areas for enhancement, propose solutions, and actively participate in implementing changes. Open communication is key - make sure everyone feels heard and valued. By adopting a cycle of identifying, implementing, and standardizing improvements, you can stay ahead of evolving threats and strengthen your digital safeguards over time.
Conclusion: Key Takeaways
Digital safeguarding tools play a crucial role in protecting vulnerable children and enhancing nonprofit operations. As discussed, effective digital safeguarding goes beyond meeting compliance requirements - it directly supports and empowers your mission. These tools not only secure sensitive data but also contribute to the growth and success of your organization.
Benefits of Digital Safeguarding Tools
The advantages of digital safeguarding tools extend well beyond basic protection measures. With features like AI-driven algorithms, real-time tracking, and secure digital identities, these tools enable faster detection of abuse, proactive prevention strategies, and smarter allocation of resources. For instance, AI systems excel at identifying harmful content and preventing abuse on a large scale.
The scope of these tools is expansive. Virtual reality simulations, for example, help teach children how to navigate dangerous situations safely. Meanwhile, blockchain technology ensures secure and tamper-proof digital identities, reducing the risk of identity fraud. Additionally, data-driven insights allow authorities to identify children at risk early on, enabling more targeted and effective prevention efforts.
These tools also process immense amounts of data that would be impossible for humans to handle alone. They filter harmful content, detect predatory behavior, and provide educational resources - all at the same time. This capability is especially critical, considering that half of NGOs, including the International Committee of the Red Cross, have experienced cyberattacks.
Final Thoughts on Choosing the Right Platform
With these benefits in mind, nonprofits must carefully select platforms that secure sensitive data while supporting operational goals. Despite 74% of nonprofits acknowledging the need for digital transformation, only 12% have successfully achieved it. Choosing a platform that aligns with your organization’s needs and can scale with your growth is essential. Digitally advanced nonprofits are four times more likely to achieve their mission goals and double their operational efficiency.
When evaluating platforms, consider your organization's specific vulnerabilities, budget, and long-term goals. A well-chosen platform not only safeguards data but also enhances communication with supporters and stakeholders.
HelpYouSponsor is one such solution, offering scalable tools for safeguarding, sponsorship management, and donor engagement. Designed by experts with firsthand experience in running sponsorship programs, it addresses the unique challenges nonprofits face while maintaining the necessary security standards to protect sensitive information.
Investing in the right tools can lead to transformative results. Nonprofits with advanced analytics capabilities report a 78% boost in mission effectiveness. This demonstrates how proper digital safeguarding tools can significantly enhance both protection and operational success.
"AI acts as a guardian of the digital playground, ensuring it remains a space of safety and growth for children." - Neil Sahota, Former Contributor, Forbes
FAQs
How do digital safeguarding tools help nonprofits protect sensitive data and comply with privacy regulations?
Digital safeguarding tools are essential for nonprofits to protect sensitive information and comply with privacy laws. These tools incorporate advanced security features like encryption, firewalls, and secure databases to shield personal data from breaches or unauthorized access.
They also assist organizations in performing regular risk assessments and implementing strict access controls, ensuring only authorized individuals can handle sensitive data. By simplifying adherence to regulations such as GDPR and other privacy standards, these tools help minimize risks, allowing nonprofits to operate safely and responsibly.
What should nonprofits look for in a digital safeguarding platform?
When selecting a digital safeguarding platform, nonprofits should focus on a few essential features to keep sensitive information secure. Start with strong encryption, user access controls, and adherence to data protection laws - these are non-negotiable for safeguarding data. Additionally, tools like customizable reporting, real-time monitoring, and data backup and recovery can simplify incident management and ensure your operations run smoothly, even in challenging situations.
Another crucial factor? A user-friendly interface. This makes it easier for your team to get comfortable with the platform and respond to safeguarding issues efficiently. By prioritizing these features, your organization can protect its data and meet compliance standards with ease.
What are the best ways for nonprofits to train their staff to use digital safeguarding tools and identify cyber threats?
Nonprofits can equip their staff to handle digital threats by providing regular cybersecurity training. These sessions should cover common risks such as phishing scams, ransomware attacks, and social engineering tactics. Adding interactive components, like simulated phishing exercises, can help employees better recognize and respond to potential threats.
It's also important to encourage continuous learning to stay ahead of new and evolving cyber risks. Regular cybersecurity audits can help uncover weak spots in your systems. By fostering a mindset of vigilance and prioritizing digital safety, your team will be better prepared to use safeguarding tools effectively and protect your organization’s digital assets.