Top 7 Tools for Secure Donor Data Storage
Learn about the top tools for secure donor data storage to protect sensitive information and ensure compliance with regulations.

Nonprofits face growing cybersecurity threats, with data breaches costing up to $2 million and cyberattacks surging by 30% in 2024. Protecting donor data is critical to maintaining trust, meeting compliance (e.g., GDPR, CCPA), and avoiding financial disaster. Here are 7 secure donor data storage tools that offer encryption, compliance support, and access controls:
- HelpYouSponsor: Free for small programs, encrypts data end-to-end, and tracks donations securely.
- Zeffy: Free platform with AWS/Heroku infrastructure, 2FA, and compliance with GDPR, CCPA.
- DonorPerfect: Starting at $99/month, offers multi-factor authentication and PCI compliance.
- Bloomerang: $119/month with custom permissions and donor retention tools.
Quick Comparison
| Tool | Starting Price | Key Features | Best For |
|---|---|---|---|
| HelpYouSponsor | Free (up to 10) | End-to-end encryption, donation tracking | Sponsorship programs |
| Zeffy | Free | AWS/Heroku, 2FA, GDPR/CCPA compliance | Budget-conscious nonprofits |
| DonorPerfect | $99/month | Multi-factor authentication, PCI compliance | Comprehensive donor management |
| Bloomerang | $119/month | Custom permissions, retention focus | Mission-driven organizations |
Key Takeaway: The right tool balances security, compliance, and ease of use while fitting your nonprofit's budget and needs.
Data Security & Cyber Attacks | Donor Data & Nonprofit Fundraising | The Nonprofit Podcast 138
What to Look for in Secure Donor Data Storage Tools
With the risks of data breaches being so high, choosing a donor data storage tool isn't something to take lightly. The right platform can safeguard sensitive information and help you stay compliant with regulations. Here's a breakdown of the key features to keep in mind.
Data Encryption and Access Controls
Encryption is the backbone of any secure data storage system. Abby Jarvis explains it perfectly:
"When your data is encrypted, it is converted into a code that can only be deciphered with a specific key. This means that even if a hacker gains access to your data, they won't be able to read it without the encryption key."
Your tool should encrypt donor data both in transit and at rest. Look for platforms that integrate encryption into every aspect - whether it’s fundraising systems, donor management databases, email programs, or website interactions. Ask about the specific encryption methods used, and ensure the platform supports secure protocols like HTTPS, SFTP, SSL, or TLS 1.2+. High encryption standards are non-negotiable.
Access controls are another critical layer of protection. Features like two-factor authentication (2FA) and role-based access controls (RBAC) help limit access to sensitive donor data. The platform should allow you to assign access permissions based on staff roles, restricting who can view or modify specific database fields or records. Additional safeguards like IP address restrictions and the ability to revoke access immediately for former employees are must-haves.
Compliance Standards and Certifications
Nonprofits face a maze of privacy regulations, from GDPR and CCPA to state-specific laws. The right donor data storage tool should make navigating these requirements easier. Look for platforms that support opt-in consent processes and track compliance details at the individual donor level. This includes keeping records of when and how donor information was collected, which simplifies audits and compliance checks.
A good platform will also help you implement privacy policies by clearly documenting data collection and usage practices. Since regulations are constantly evolving, choose a tool that stays updated with the latest legal requirements and provides guidance on best practices. It’s worth working with the platform's support team or a nonprofit technology consultant to ensure all compliance needs are met for your organization.
Activity Tracking and Data Backup
Security isn’t just about prevention - it’s also about monitoring and recovery.
Audit trails are a key feature for tracking who accesses donor data and what changes are made. Your tool should automatically log activities like data updates, user logins, and access attempts. This visibility is essential for spotting suspicious behavior.
Backup systems are equally important. The platform should create automated, secure backups regularly and store them in multiple locations to protect against data loss due to attacks or system failures. Testing the backup restoration process is also essential to ensure you can recover data quickly if needed.
Given that 70% of nonprofits lack proper incident response plans, having a tool with built-in backup and recovery features is crucial. Organizations with strong incident response capabilities can save an average of $1.5 million when a breach occurs. Additionally, the platform should provide regular security updates and maintenance to address new threats, showing a commitment to keeping your data safe over time.
7 Tools for Secure Donor Data Storage
When it comes to protecting donor data, the right tools can make all the difference. Below are seven platforms that not only prioritize security but also streamline donor management.
HelpYouSponsor: Tailored Security for Sponsorship Programs
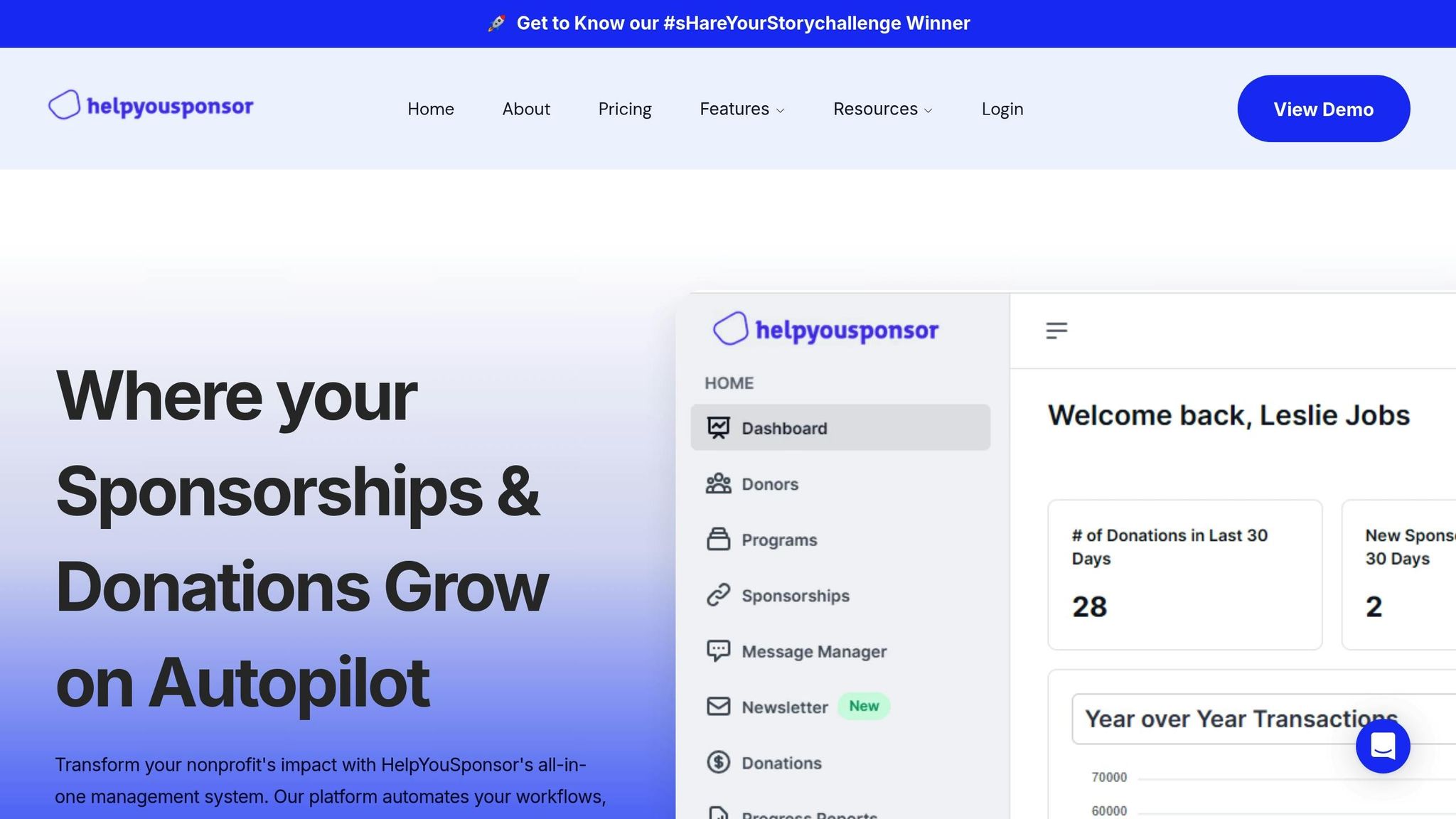
HelpYouSponsor is a comprehensive platform built specifically for nonprofits managing sponsorships and donor relationships. It tackles the unique challenges nonprofits face by encrypting sensitive donor data both in transit and at rest.
This platform provides end-to-end security for a range of campaigns, from child sponsorships to large-scale building projects. With features like integrated payment gateways and donation tracking, it safeguards financial transactions and donor information throughout the entire process.
Its donor accounts system centralizes data, tracks contributions, and automates receipt generation - all while maintaining strict encryption standards. For smaller organizations, HelpYouSponsor offers a free plan covering up to 10 commitments per month. Larger programs can opt for usage-based pricing at $0.50 per commitment.
Zeffy: A Free Option with Enterprise-Level Security
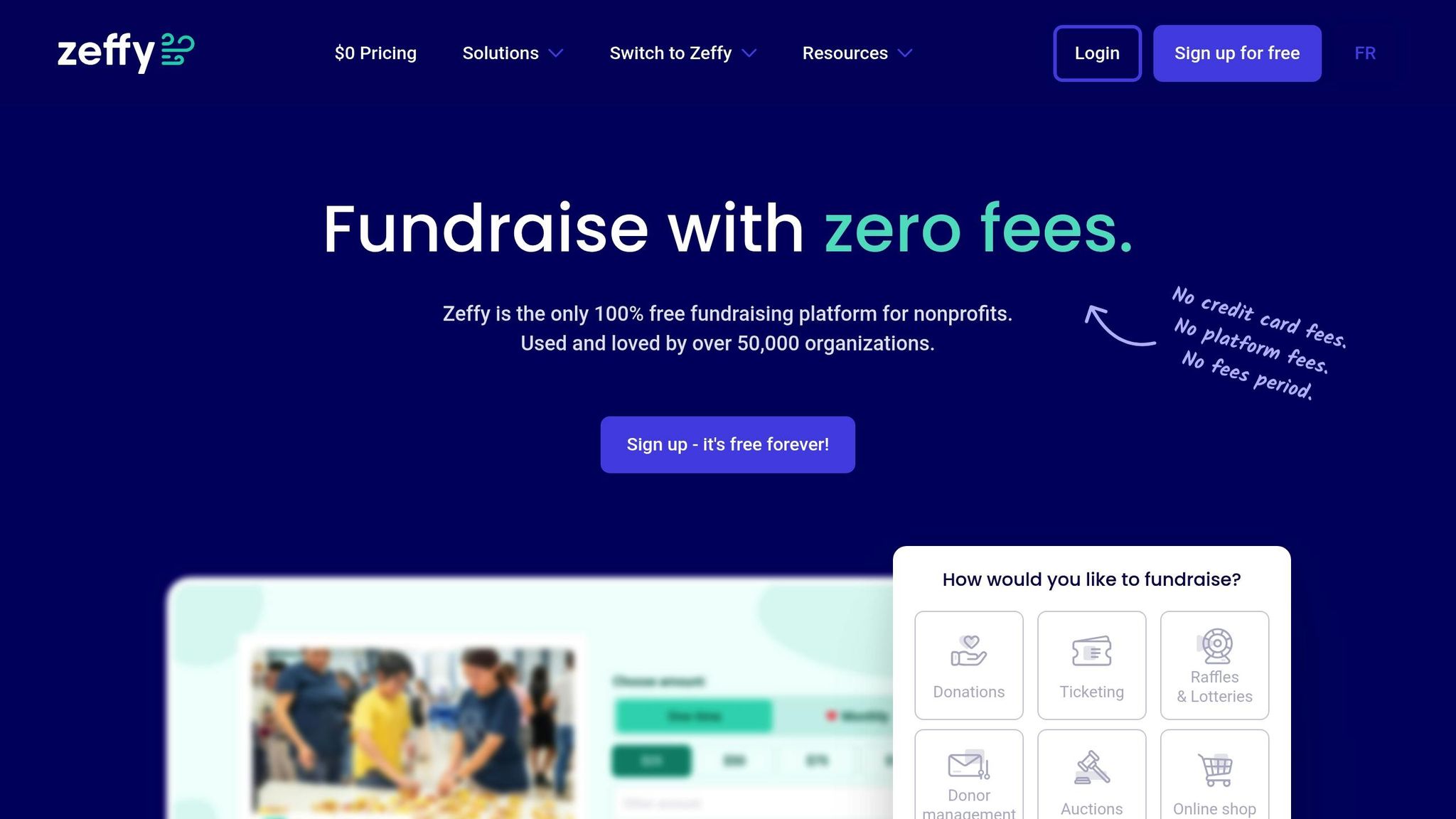
Zeffy combines zero-cost access with high-quality security measures. It uses Amazon Web Services (AWS) and Heroku for secure data storage, ensuring even free users benefit from professional-grade protections.
The platform employs SSL and TLS protocols for encryption and complies with regulations like GDPR, PIPEDA, and CCPA. Additional security features include Two-Factor Authentication (2FA) and alerts for account changes, such as new device logins or bank account updates. For payment processing, Zeffy partners with Stripe, which holds PCI Service Provider Level 1 certification.
DonorPerfect: Reliable and Centralized Data Security

With over 60,000 nonprofit professionals relying on it, DonorPerfect is a trusted choice for centralized donor data management. Its security measures include infrastructure protection, multi-factor authentication, and role-based access controls that allow for detailed activity tracking.
DonorPerfect encrypts donor and financial data during both storage and transmission. It also uses SafeSave for secure payment processing, ensuring PCI DSS compliance. Pricing starts at $99 per month, with customizable tools to fit nonprofits of all sizes.
Customizable Platforms for Specific Needs
For nonprofits with unique security requirements, platforms like Bloomerang offer tailored solutions. Starting at $119 per month, Bloomerang provides features such as granular user permissions and custom data retention policies.
These platforms also include tools like security dashboards for monitoring access, compliance-focused features, and approval workflows that allow for data segregation between programs.
Additional Security-Focused Tools
Some advanced tools go above and beyond with features like robust encryption, stringent audit processes, and PCI DSS Level 1 compliance. When evaluating platforms, nonprofits should prioritize certifications and transparent data processing agreements.
Considering that the median financial loss to nonprofits due to fraud is $100,000, investing in secure solutions is a must. Organizations should also ask about regular security audits and backup systems when choosing a donor data storage platform.
| Tool | Starting Price | Key Security Features | Best For |
|---|---|---|---|
| HelpYouSponsor | Free (up to 10 commitments) | End-to-end encryption, payment processing | Sponsorship programs |
| Zeffy | Free | AWS/Heroku infrastructure, 2FA, regulatory compliance | Budget-conscious nonprofits |
| DonorPerfect | $99/month | Multi-factor authentication, PCI compliance | Comprehensive donor management |
| Bloomerang | $119/month | Custom permissions, donor retention focus | Mission-driven organizations |
With 80% of adults worldwide expressing concerns about online privacy, robust data security is more than just a regulatory requirement - it’s key to building and maintaining donor trust.
Best Practices for Secure Donor Data Management
Protecting donor information goes beyond choosing strong security tools. It requires consistent best practices to minimize risks. Even the most advanced platforms can't fully guard against breaches caused by human mistakes or internal process flaws.
Staff Training and Security Awareness
Your team plays a critical role in safeguarding donor data. As one expert notes, "Cybersecurity awareness empowers your staff to protect sensitive donor data and maintain your organization's reputation". Training employees to spot phishing attempts, create strong passwords, and promptly report security concerns is essential.
Consider the consequences of a lapse in security. In May 2024, Ascension, a leading nonprofit, experienced a ransomware attack. This incident disrupted clinical operations, delayed procedures, and even diverted ambulances - all stemming from a single cyber event.
To stay ahead, host brief monthly security updates to review new threats and reinforce a culture where staff feel encouraged to report issues quickly.
Compliance training is equally important. Organizations handling health information or serving vulnerable populations must ensure their teams understand HIPAA regulations and know how to respond if sensitive data is compromised. These proactive efforts lay the groundwork for ongoing security evaluations.
Regular Security Reviews
Building on staff preparedness, routine security reviews are key to identifying and resolving vulnerabilities. Cyber threats evolve constantly, so your organization must keep pace through consistent monitoring and updates.
Schedule annual vulnerability tests, enforce automatic software updates, and log network activity to detect irregularities promptly. These tests often reveal issues like outdated software or poorly managed access permissions.
Risk assessments should occur at least once a year, with additional reviews following major changes in systems or staffing. Evaluate who has access to sensitive data, how information flows within your organization, and where critical data is stored. Document these findings and develop action plans to address any weaknesses.
Staying informed about trends in cyberattacks targeting nonprofits can also provide valuable insights. Learning from other organizations' experiences helps you anticipate and prepare for similar threats.
Security Breach Response Planning
Even with the best precautions, breaches can still happen. The cost of a breach often depends on how quickly it's detected and addressed, making a well-prepared response plan essential. This plan should outline clear steps for containing the damage, notifying stakeholders, and conducting a thorough post-incident review.
When a breach occurs, activate your response team immediately. This team should include representatives from forensics, legal, IT, HR, communications, and management. Time is of the essence - every moment counts in limiting the scope of the breach.
Start by focusing on containment. Secure physical areas tied to the breach, stop further data loss by disconnecting affected systems, update user credentials, and remove any exposed information from public access. Be sure to document and preserve all evidence for further investigation.
Real-world cases highlight the importance of a swift response. For example, in May 2019, a New York social services agency discovered hackers had accessed two employee email accounts. This breach potentially exposed sensitive data, including Social Security numbers and medical records, for over 1,000 clients. The agency quickly reset the compromised account passwords.
After containing the breach, communication becomes a priority. Identify legal notification requirements, inform law enforcement, and notify affected individuals and organizations. A single point of contact should manage all external communications to ensure consistent messaging. Offering free credit monitoring or identity theft protection to those affected can also help rebuild trust.
Your communication should explain what happened, what information was exposed, the steps taken to resolve the issue, and what individuals can do to protect themselves. Encourage those impacted to report any misuse of their information to the FTC.
Finally, regularly test your breach response plan through simulated scenarios. These exercises can uncover weaknesses in your plan and ensure your team is prepared to act quickly and effectively when faced with a real incident.
Conclusion: Selecting the Right Tool for Your Organization
Choosing the right donor data storage tool is a critical decision, especially when balancing security, regulatory compliance, and the unique needs of your organization. The stakes are enormous - data breaches surged by 78% in 2023, with the average cost of a single breach hitting $4.45 million. For nonprofits operating on tight budgets, even one security incident could have catastrophic consequences. This financial risk makes selecting the right tool an absolute priority.
The challenges are compounded by concerning trends in nonprofit cybersecurity: 38% of nonprofits lack formal cybersecurity policies, 68% don’t have documented responses to attacks, and 56% fail to use multi-factor authentication. These gaps not only increase vulnerability but also jeopardize donor trust and compliance with regulations.
When evaluating donor data storage tools, prioritize features like strong access controls (e.g., two-factor authentication, role-based permissions), robust data protection (e.g., PCI compliance, encryption, tokenization), and integration capabilities that align with your existing systems. Look for software specifically designed for nonprofits - 70% of nonprofits report higher satisfaction with solutions tailored to their sector. Additionally, organizations that include stakeholders in the decision-making process see a 70% boost in satisfaction rates.
Don’t overlook costs associated with implementation, training, and ongoing maintenance - many providers offer discounts for nonprofits. The right solution should not only safeguard sensitive donor data but also scale with your organization’s growth, whether you’re a small volunteer-led group or a large nonprofit managing complex programs.
Ultimately, secure donor data storage isn’t just about meeting compliance standards. It’s about protecting your organization’s future and preserving the trust of the donors who make your mission possible.
FAQs
What should nonprofits look for in a donor data storage tool to stay compliant with regulations like GDPR and CCPA?
Nonprofits need tools that help them stay compliant with privacy laws like GDPR and CCPA. This means focusing on features that support transparent data collection, require explicit donor consent, and enable data access and deletion requests. These capabilities not only fulfill legal obligations but also help build and maintain trust with donors.
It's equally important to choose tools with robust cybersecurity measures. Look for encryption, multi-factor authentication, and secure access controls to protect sensitive donor data. Regular security audits and staff training on data protection practices can add an extra layer of security, ensuring compliance while safeguarding donor information.
How do encryption and access controls help protect donor data from cybersecurity threats?
Encryption and Access Controls: Protecting Donor Data
Keeping donor data secure is non-negotiable, and two key tools in this effort are encryption and access controls.
Encryption works by transforming sensitive information into a scrambled, unreadable format. Only those with the correct decryption key can make sense of it. This means that even if someone intercepts the data, it’s essentially useless without proper authorization - a crucial safeguard against cyber threats.
On the other hand, access controls focus on limiting who can interact with donor data. This includes enforcing strong password policies, implementing multi-factor authentication, and using role-based permissions to ensure individuals can only access information relevant to their job. These measures create an extra barrier, helping to keep sensitive information out of the wrong hands.
By combining encryption with robust access controls, organizations can better protect donor data, ensuring it remains both confidential and secure.
Why do nonprofits need a security breach response plan, and what should it include?
The Importance of a Security Breach Response Plan for Nonprofits
Having a security breach response plan is crucial for nonprofits to safeguard sensitive donor information and uphold trust. Cyber incidents can disrupt daily operations, cause financial setbacks, and tarnish an organization’s reputation. A well-thought-out plan ensures a quick, organized response, reducing potential damage and helping nonprofits get back on track efficiently.
A solid response plan should clearly define key roles and responsibilities, establish communication protocols, and outline a chain of command. It must also include detailed steps for identifying, containing, and recovering from breaches, along with guidance to comply with legal and regulatory obligations. By taking these proactive measures, nonprofits can not only address immediate threats but also build stronger defenses for the future.